
“They Had a Photo of My Children”: The Jeffery Delisle Case, Part II
(NOIR For USA) If it was former Canadian Navy Sub-Lieutenant Jeffery Delisle’s intention to free himself of the burden of his financial troubles and to take some decisive action to

(NOIR For USA) If it was former Canadian Navy Sub-Lieutenant Jeffery Delisle’s intention to free himself of the burden of his financial troubles and to take some decisive action to

(Federal News Radio) For the past six months, the Director of National Intelligence has been trying to determine whether the government should do Google searches on people who hold security

(CNET) The Russian government uses malware to extract sensitive information from companies and governments, not for financial gain but for intelligence gathering, according a new report by FireEye. Malicious software designed

(Washington Post) A coalition of security researchers has identified a Chinese cyberespionage group that appears to be the most sophisticated of any publicly known Chinese hacker unit and targets not

(NOIR For USA) By all accounts, there’s nothing exceptional about former Canadian Navy Sub-Lieutenant Jeffery Delisle, certainly nothing that would suggest a future as a convicted insider spy. A high

The following video is making its rounds because it warns people about the dangers of downloading free flashlight apps on your smartphone. The makers of these apps get your permission

(DNI) The Director of National Intelligence James R. Clapper today unveiled the 2014 National Intelligence Strategy – the blueprint that will drive the priorities for the nation’s 17 Intelligence Community

(Reuters) Hackers associated with the Chinese government have repeatedly infiltrated the computer systems of U.S. airlines, technology companies and other contractors involved in the movement of U.S. troops and military

Hawaii Man Sentenced to 87 Months Imprisonment for Communicating Classified National Defense Information to Unauthorized Person Wednesday, September 17, 2014 (DOJ) Assistant Attorney General for National Security John P. Carlin
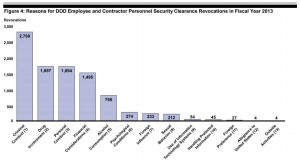
The United States Government Accountability Office (GAO) just issued a report called, PERSONNEL SECURITY CLEARANCES: Additional Guidance and Oversight Needed at DHS and DOD to Ensure Consistent Application of Revocation

(New York Times) T-Mobile has filed a lawsuit against the Chinese smartphone maker Huawei Technologies, accusing the manufacturer of stealing technology, including part of a robot’s arm, from T-Mobile’s Bellevue,

(Newsweek) The continuing leaks of National Security Agency material by Edward Snowden so dominate the news that you don’t hear much these days about Cold War–style moles burrowing through the CIA,
Security Educator
Public Speaker
Motivator
National Security Expert
“On a scale of 1 to 10, this DICE briefing was a 20!”–Corporate CEO
You must be logged in to post a comment.